Google fixes critical CSRF flaw in the default share buttons on Blogspot domain which would have allowed attackers to hijack blogsDiscoveryTimelineVideo
Discovery
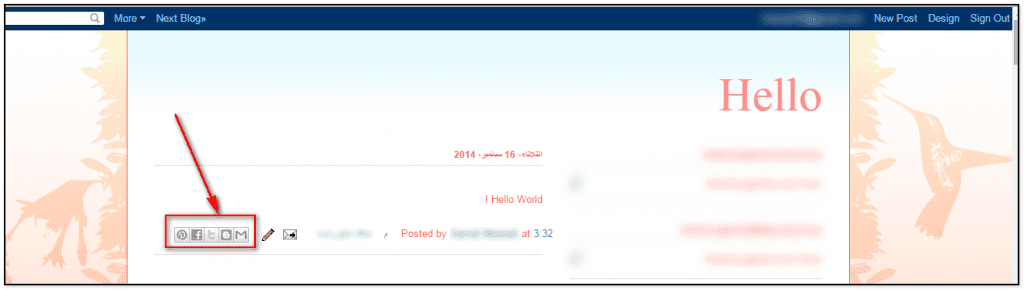
Below the steps followed by the Mesbah to discover the flaw:
I found the vulnerability in Button of Share Articles in blog as shown in the following picture. When I noticed this button I decided to investigate the possible presence of a flaw affecting it. When I click on Blogger Share button I noticed the CSRF token the Request, then I tried to bypass the mechanism of authentication based on it. I succeeded in the trick. Once verified the presence of the flaw I wrote an exploit file that could be used against any blog just knowing the Blog ID. The Blog ID is easy to retrieve, I discovered an easy way to access it. Once completed the exploit I tested it against the Blogger platform and I verified that it was working.
Timeline
The timeline for the above vulnerability is reported below: 2/9/2014 – The vulnerability was found and report by Mazen Gamal Mesbah to Google. 2/9/2014 – Response received from the Blogger team acknowledging the vulnerability 3/9/2014 – The vulnerability was patched 4/9/2014 – A reward aka bounty of $3133.7 was received by the researcher for pointing out the vulnerability
Video
Mesbah has uploaded a video detailing how he found out the vulnerability, which is given below :
Resource : Security Affairs.